A password checker is a web tool that helps you evaluate your password strength. It analyses the syntax of your password and informs you about its weaknesses. Also, it checks the database of breached passwords and flags if your passwords have been compromised in any brute-force or dictionary attacks. ↓ 08 – Personal Data Leak Checker. Welcome to your Password Manager. Manage your saved passwords in Android or Chrome. They’re securely stored in your Google Account and available across all your devices. Password Checkup. Check the strength and security of your saved passwords. Find out if they’ve been compromised and get personalized advice when you need it.
Your data is safe in 1Password. Fundamental design choices were made to protect everything you store in 1Password so you can trust it with your passwords, financial information, and more. 1Password protects you and your information in three different ways:
- End-to-end encryption leaves the keys in your hands – and nowhere else.
- Smart features limit your exposure to threats outside 1Password.
- Full transparency makes sure 1Password can be and is audited by experts.

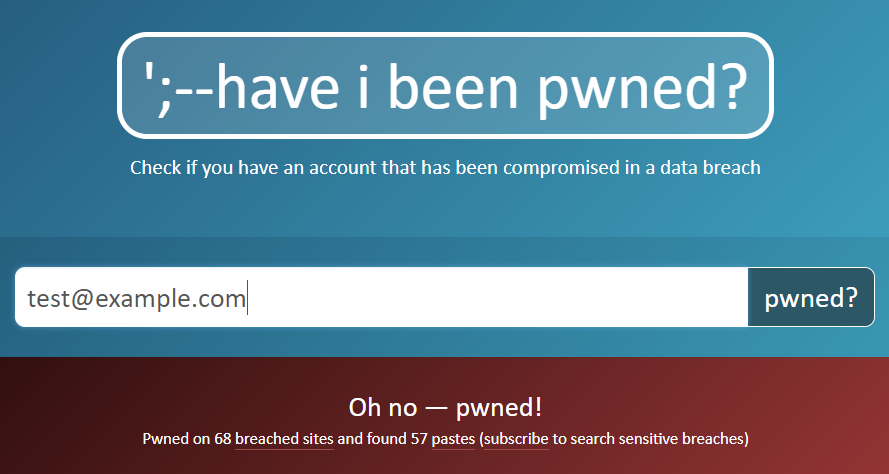
1password Compromised Website Password
Encryption

1Password security begins with your Master Password. It’s used to encrypt your data, so no one but you can read it. It’s also used to decrypt your data when you need it. Your Master Password is never shared with anyone, even us at AgileBits, which means that you’re the only person who can unlock your 1Password vaults and access your information. Here’s how 1Password secures your data – and the Master Password used to protect it – from all kinds of attacks:
End-to-end encryption. Whether you use a 1Password account or sync your data with iCloud or Dropbox, everything is always end-to-end encrypted. This makes it impossible for someone to learn anything by intercepting your data while it’s in transit or even obtaining it from AgileBits. Learn more about how 1Password protects your data when you use a sync service.
256-bit AES encryption. Your 1Password data is kept safe by AES-GCM-256 authenticated encryption. The data you entrust to 1Password is effectively impossible to decrypt.
Secure random numbers. Encryption keys, initialization vectors, and nonces are all generated using cryptographically secure pseudorandom number generators.
PBKDF2 key strengthening. 1Password uses PBKDF2-HMAC-SHA256 for key derivation which makes it harder for someone to repeatedly guess your Master Password. A strong Master Password could take decades to crack. Learn more about how PBKDF2 strengthens your Master Password.
A secret Master Password. Your Master Password is never stored alongside your 1Password data or transmitted over the network. Taking this precaution is a bit like making sure the key to a safe isn’t kept right next to it: Keeping the two separate makes everything more secure. The same principle applies here.
Secret Key. The data in your 1Password account is protected by your 128-bit Secret Key, which is combined with your Master Password to encrypt your data. Learn more about your Secret Key.
Features
Security doesn’t end with encryption. 1Password was designed to protect your data in other ways, too, whether it’s by automatically clearing your clipboard or making sure your Master Password can’t be stolen. Here are just some of the other ways 1Password keeps your data safe:
Clipboard management. 1Password can be set to automatically remove passwords from your clipboard. This prevents anyone from gaining access to your data by pasting a password you copied and forgot about. It also means that tools that save your clipboard history don’t store your secrets.
Code signature validation. 1Password verifies that your browser has been signed by an identified developer before filling your sensitive information. This protects you if your browser is tampered with, or if you try to use a browser that hasn’t been proven secure.
Auto-lock. 1Password can automatically lock to make sure that no one can access your data when you’re away from your desk or after closing the lid on your laptop. Learn how to set 1Password to lock automatically.
Secure input fields. 1Password uses secure input fields to prevent other tools from knowing what you type in the 1Password apps. This means that your personal information, including your Master Password, is protected against keyloggers.
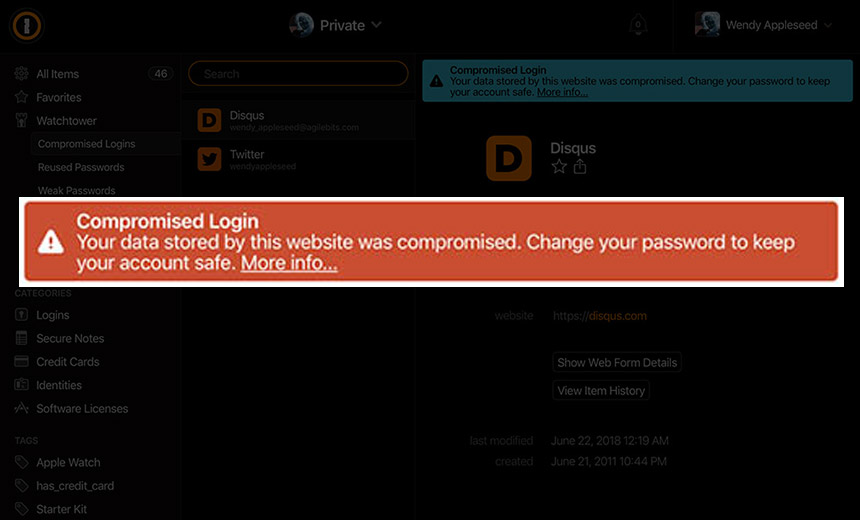
Watchtower vulnerability alerts. 1Password can warn you when a website has been hacked – without ever sending AgileBits a list of the websites you visit. Learn more about how Watchtower protects your privacy.
Phishing protection. 1Password only fills passwords on the sites where they were saved. No one can steal your password by pretending to be a site you trust.
Your input, required. 1Password only displays or fills data when you tell it to. Whether you’re revealing a password or filling your shipping address in your browser, your personal information is never displayed or filled without your command.
Biometric access. You can unlock 1Password with your fingerprint on your Mac with Touch ID, iPhone, iPad, and Android devices. This makes accessing your information more convenient, and also means that someone can’t learn your Master Password by peering over your shoulder. Learn more about biometric security on Mac, iOS, and Android.
Transparency
1Password wasn’t built in a vacuum. It was developed on top of open standards that anyone with the right skills can investigate, implement, and improve. Open tools are trusted, proven, and constantly getting better. Here’s how 1Password respects the principles behind the open tools on which it relies:
Open data formats. 1Password uses two open data formats for all your information. These data formats are available to anyone who wants to examine them to prove that they do what they say they do. Learn more about the designs of OPVault and Agile Keychain.
Trusted encryption algorithms. 1Password uses algorithms that experts have examined and verified to keep information secure.
Principled privacy policy. 1Password was designed with a deep respect for your privacy. Any information you share with us is only ever used to provide you with service and support. Learn more about 1Password and your privacy.
Straightforward export tools. 1Password includes simple export tools that make it easy to move information out of 1Password. Your data is yours, and you can leave if ever you choose to. Learn more about how to export data from 1Password.
Learn more
If you have a security concern, contact 1Password Support with more information.
Google introduced a new Chrome extension which will automatically and securely check whether user passwords have been exposed in a data breach.
Called Password Checkup, the Chrome extension is Google's attempt to address the problem of password reuse on the Web. When the user attempts to log in to a website or application via the Chrome browser, the extension checks the password against an internal Google database containing billions of already-compromised login credentials. If the password has been compromised, the user will be alerted and prompted to create a new password.
'If we detect that a username and password on a site you use is one of over 4 billion credentials that we know have been compromised, the extension will trigger an automatic warning and suggest that you change your password,' wrote Google research scientist Kurt Thomas and product manager Adam Dawes in the announcement.
Google said most U.S. websites are supported.
In the event of a data breach where passwords are stolen, users who already use unique passwords for each web application or service have less to worry about compared to those who reuse passwords. All they have to do is change that one password. Reusing passwords means having to change the password for every site that used the now-breached password.
Attackers take credentials stolen in data breaches and try to use them on popular online services, such as email, social media, retail, and financial services accounts to see if they can get access. The more places a password is used, the more likely these attackers will succeed in their attempts.
The number of password breaches also makes it difficult for individual users to stay on top of every incident and make sure they are changing the passwords right away. And just because the breach was a long time ago doesn’t mean the criminals won’t try. There is a collection of 2.2 billion passwords, some dating as far back as 2008, being passed around on criminal forums. Even if less than 1 percent of the passwords were still valid, that’s millions of accounts that could potentially be taken over.
1password Compromised Website Alert
Despite frequent reminders to not reuse passwords, the problem is still prevalent. A Harris Poll commissioned by Google surveyed 3,000 adults in the United States to understand what they think about online security and what they actually do. While 69 percent of people in the poll thought they did a good job protecting their online accounts, their actual behaviors suggested otherwise. Even though 59 percent felt their accounts were safer than those of the “average Internet user,” 65 percent reused the same password across multiple sites. The poll found that 51 percent had a favorite password they used for most sites. Only 24 percent of users in the poll said they used a password manager.
This service would help improve overall online security, but Google doesn’t ask users to hand over passwords to other sites—that would be asking for too much trust. Instead, Password Checkup relies on a combination of anonymization and cryptography to ensure that user credentials are not visible to Google. User credentials being entered on the site—either manually by the user into the login screen or by Chrome’s built-in password manager—are anonymized with an Argon2 hash function to create a search key for the password database, and also encrypted with elliptic curve cryptography. A technique called blinding create a secret search index to use on the database. The passwords are stored in the database in a hashed and encrypted form so someone at Google won’t be able to look at the values. The alerts are local to the machine the extension is visible on, so Google won’t be able to track which passwords had to be changed.
'We built Password Checkup so that no one, including Google, can learn your account details,' Dawes and Thomas wrote.
Google isn’t really breaking new ground with checking passwords against a database of passwords collected from previous data breaches. Facebook, Netflix, and Microsoft are known for checking user credentials against known breaches. If the user tries to use a password combination that was already in a breach to log in to the sites, the sites alert the user and prompt for a change. Google does the same for its G Suite users—except it references its own internal database that Google’s threat research team compiled by trawling through data dumps and criminal forums. The database has currently over 4 billion compromised credentials.
'We already automatically reset the password on your Google Account if it may have been exposed in a third party data breach—a security measure that reduces the risk of your account getting hacked by a factor of ten,' Thomas and Dawes wrote.
What the company is doing differently with Password Checkup is that it is providing the checking service for sites and applications outside its own ecosystem.
Mozilla does something similar with Firefox Monitor service, which notifies users if the site they are visiting has been part of a data breach. Firefox Monitor relies on security researcher Troy Hunt’s Have I Been Pwned to find out if user information has been compromised. Password managers such as LastPass and 1Password also rely on the Have I Been Pwned database.
Checking against known data breaches rather than dictionaries or lists of commonly used passwords is more effective “because it checks what real people have actually used in the past,” cryptography expert Kenn White wrote on Twitter. White noted that the latest NIST 800-53 guidance on “memorized secrets” recommends checking public breach databases.
